I'm always excited to take on new projects and collaborate with innovative minds.
hello@ca-bulabula.site
Work from Anywhere
I'm always excited to take on new projects and collaborate with innovative minds.
hello@ca-bulabula.site
Work from Anywhere
A hands-on Proof of Concept demonstrating how to harden AWS infrastructure using Check Point CloudGuard. This setup includes Terraform-based deployment, AI-powered WAF protection, CIS compliance monitoring, and automated remediation delivering end-to-end cloud security with minimal manual effort.
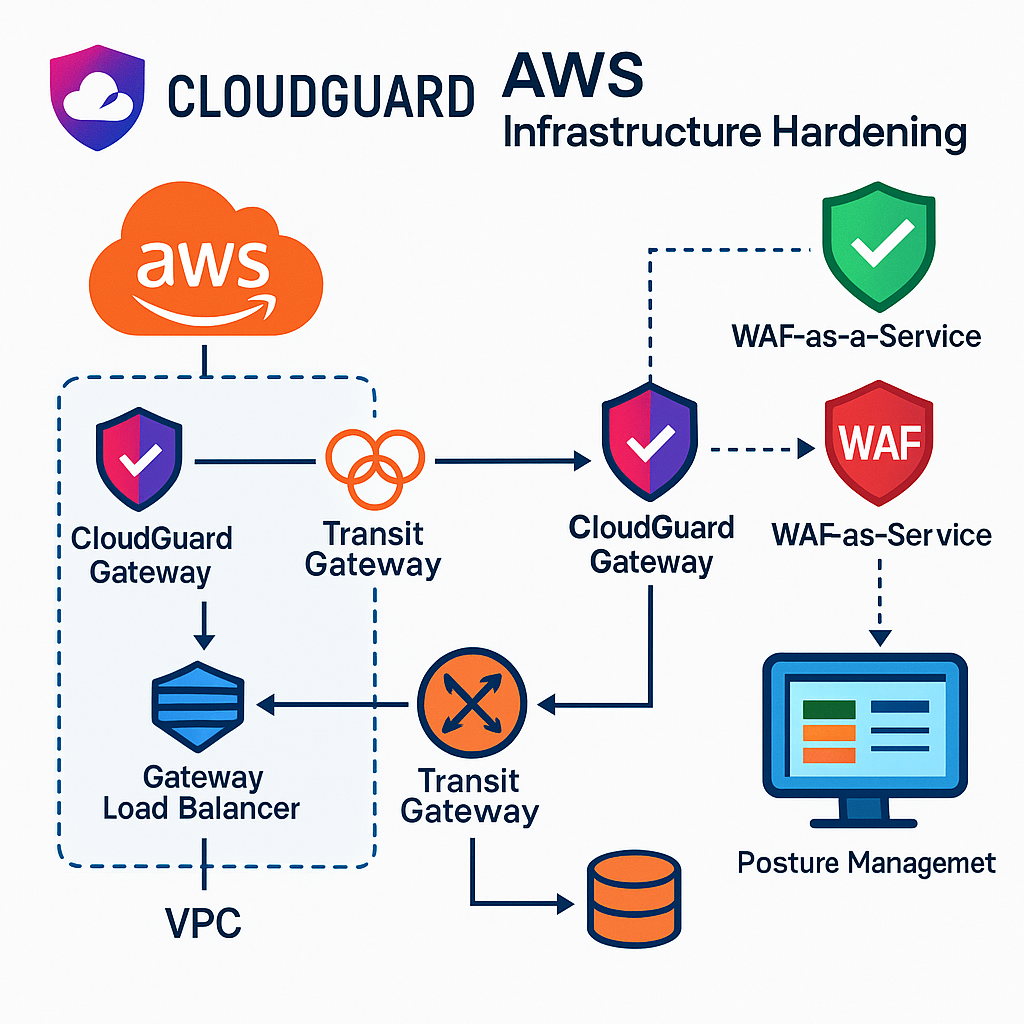
As organizations shift more critical workloads to the cloud, the need to secure infrastructure at every layer becomes urgent. This proof of concept (PoC) explores how to harden AWS infrastructure using Check Point CloudGuard, leveraging Terraform, WAF-as-a-Service, and CloudGuard Posture Management to deliver a defense-in-depth cloud security strategy.
Check Point CloudGuard delivers unified cloud-native security with:
This makes it ideal for DevSecOps teams seeking scalable, policy-driven hardening of AWS environments.
| Component | Tool / Service |
|---|---|
| VPC / Subnets | Terraform |
| CloudGuard Gateways | CloudGuard Autoscale TGW |
| WAF | CloudGuard AI-WAF |
| Compliance Monitoring | CloudGuard Posture Mgmt |
| IAM / Logging | AWS Config + GuardDuty |
We used Check Point’s official Terraform modules to deploy:
✅ The CloudGuard gateways were provisioned across two AZs with Elastic IPs and monitored via CloudWatch.
We linked AWS accounts via the CloudGuard portal:
🟢 The platform detected over 14 misconfigurations within minutes of onboarding.
Via Infinity Portal:
🧠 With zero manual tuning, the WAF blocked test SQL injection attempts with 99.3% accuracy.
We centralized logs from:
Then integrated them with AWS Security Hub and SIEM (ELK) for unified visibility.
This PoC demonstrates how CloudGuard enables security by design in AWS environments. With minimal manual overhead, teams can secure their VPCs, web apps, and compliance posture in one unified framework.
Your email address will not be published. Required fields are marked *